Before we begin to discuss about Fargate and its security in this blog, let’s begin with few basic concepts of container and orchestration platform.
Container
Containers provide a standard way to package your application’s code, configurations, and dependencies into a single object. Containers share an operating system installed on the server and run as resource-isolated processes, ensuring quick, reliable, and consistent deployments, regardless of environment. Whether you deploy locally on your laptop or to production, the experience will remain the same (except for secrets and other environmental values, of course).
Some other benefits of containers include:
- Speed
- Workload Isolation
- Single artifact to test from local to production, avoid drift
Container Orchestration
Container Orchestration in simple words is automating various predictable and repetitive task around running container such as patching, restart crashed containers automatically, scale as per the load, deploy containers evenly on all available nodes.
Even small applications in organizations run on multiple containers, without orchestration, it become tedious and involves lot of admin efforts. Container orchestration platforms provide you with a mechanism for managing the lifecycle of containers and ensuring the repetitive tasks are managed intelligently. Container Orchestration Platform can be created using opensource tools which requires installation and configuration.
Kubernetes, Redhat Openshift, Docker Swarm, Rancher is the most common self-managed orchestration platform. However, cloud providers like AWS offers managed orchestration platform services like ECS and EKS. Here Cloud providers take care of installation, configuration, and operations of orchestration platform whereas developers/applications owners only consume it for running containers. This saves lot of efforts and time as compared to self-managed orchestration platform.
AWS Fargate
Earlier to introduction of Fargate in 2017, EC2 Cluster/node was the only option to be used as compute engine to run containers using ECS or EKS. This required users to provision, scale, monitor, secure and manage the underlying EC2 instances themselves giving flexibility to have granular control at the cost of management tax. With Fargate, the hardware and virtual machines on which your containers run are managed completely by AWS as a "serverless" service. Fargate makes it easy for you to focus on building your applications. It removes the need to provision and manage servers, and lets you specify and pay for resources per application. The services are so convenient that many people leave them unattended, risking exposure to vulnerabilities inside their containers that can exfiltrate secrets, compromise business data, impact performance, and increase their AWS costs.
For example, think of some credentials mistakenly included in an image, later deployed on Fargate. They will be exposed to anyone with access to the image (think on the repository), or to the Fargate service.
Challenge - Security of AWS Fargate
While serverless environments free you to focus on modern application development there are also some challenges to be addressed. Serverless environments introduce an abstraction layer that hides the underlying infrastructure from the DevOps and security teams. Abstraction is blessing and as well as curse. Without access to the host or traditional monitoring tools, your visibility into workload activity can be limited, leaving you blind to threats. Once you identify a security or performance issue, teams need a detailed record of activity to respond to incidents and troubleshoot issues.
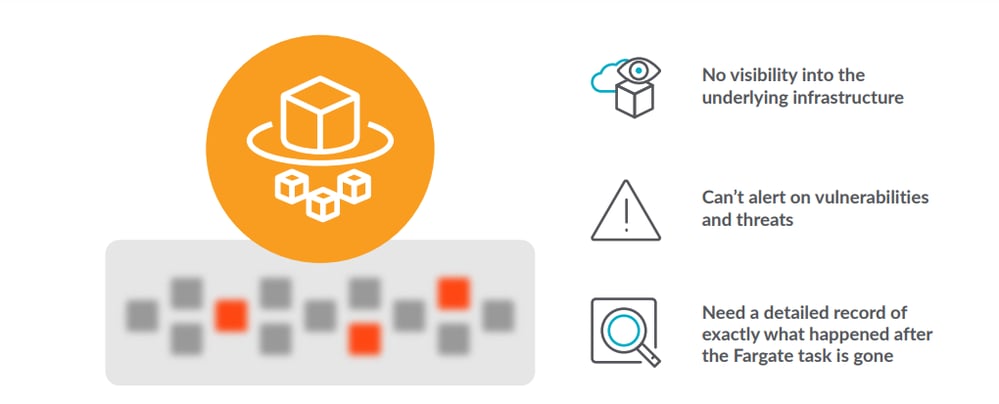
In addition, application team can use unvetted third-party images without approval where we require visibility.
Sysdig - Secure Your AWS Fargate
Sysdig provides runtime security detection and response solution, file integrity monitoring (FIM) capability to pass PCI compliance with unified view across AWS Fargate Security Posture, Vulnerabilities and Threats on compatible container services like Amazon Elastic Container Service (Amazon ECS) and Amazon Elastic Kubernetes Service (Amazon EKS).
Sysdig’s runtime detection for AWS Fargate is based on open-source Falco, the runtime security tool created by Sysdig. The deep visibility is possible through Falco’s comprehensive access to system calls exported by the Linux kernel. Sysdig worked with AWS to provide comprehensive visibility into AWS Fargate containers.
Sysdig’s Fargate security has two architectural components:
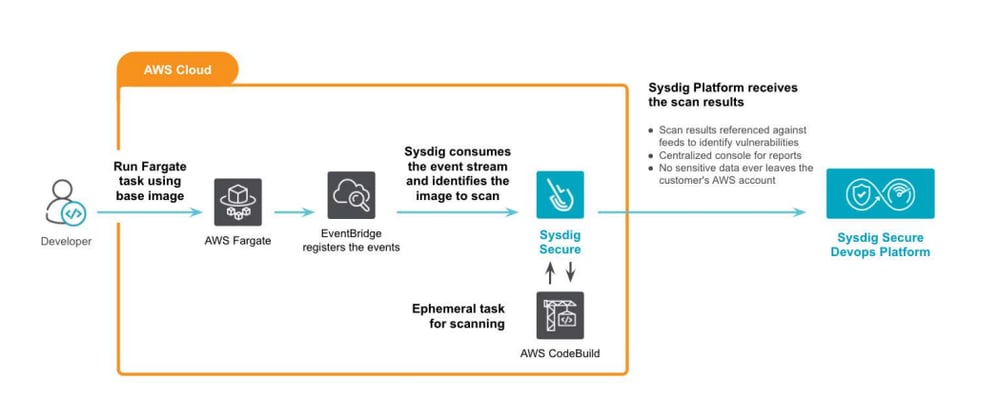
- Sysdig Fargate Image Scanning Sysdig automatically scans any container image deployed on a serverless Fargate. With this inline scanning approach, there is no need to expose or configure private AWS registries. Only image metadata / results are sent to Sysdig Secure, not the actual image contents, ensuring you protect sensitive data.
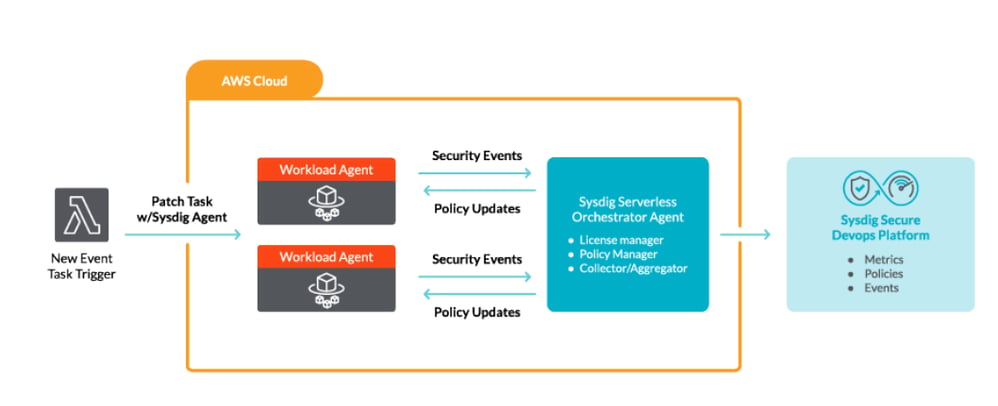
- Fargate Runtime Security the Sysdig serverless architecture provides runtime detection through policy enforcement with Falco. It consists of an orchestrator agent and a workload agent which is deployed per task. A centralized AWS Fargate task manager or orchestrator agent manages all policy, connections, and events to and from the specific AWS Fargate tasks. Teams only interact with this single entity versus keeping track of each AWS Fargate workload.
Available Sysdig products include:
- Sysdig Secure: Unified security and compliance for containers, Kubernetes, and cloud services.
- Sysdig Monitor: Monitoring for containers, Kubernetes, Prometheus, and cloud services.
- Sysdig Platform: Unified security, compliance, and monitoring (includes Sysdig Secure and Sysdig Monitor).
Sysdig in a nutshell is a SaaS platform that is simple to run in the cloud environment and can be deployed within minutes to monitor and secure serverless compute for orchestrated platform. This accelerates the adoption of container by organization by keeping their application secured from build to run stage.






