In this blog we give an overview of the implementation design of OAuth Manager using Azure Active Directory (Azure AD) and MuleSoft Anypoint Platform.
OAuth Integration Overview
What is OAuth: OAuth 2.0 has been the industry standard for securing any client facing API particularly in highly regulated industries like financial services and telecommunications. We can achieve authentication and authorization using the MuleSoft JWT policy integrated with Azure AD as the identity provider.
What is Azure AD: Azure AD acts as the Identity Provider and Client Management service, among other functionalities. As such, it supports multiple protocols like SAML, OAuth 2.0, and OpenID Connect. To implement API Authorization, we are leveraging Azure AD OAuth functionalities.
How to implement OAuth integration with Azure AD
Service Application:
- On Azure AD, create a Service application and name it -for example Service app. Select who can use the application or access the API and provide a redirect URI where the authentication response will return after the user is successfully authenticated.
- In the Service application define the Application ID URI, Scopes, Roles.
- Finally select the client applications you want authorized. This indicates to the API that it can trust these applications and users should not be asked to consent when the client calls this API.
Client on-boarding process to Azure AD - Broker Portal:
- Collect the Client’s Information.
- Client Registration: Configure the Client name, Re-direct URI, Client Secret, and granted API Permissions for the roles created in Service application.
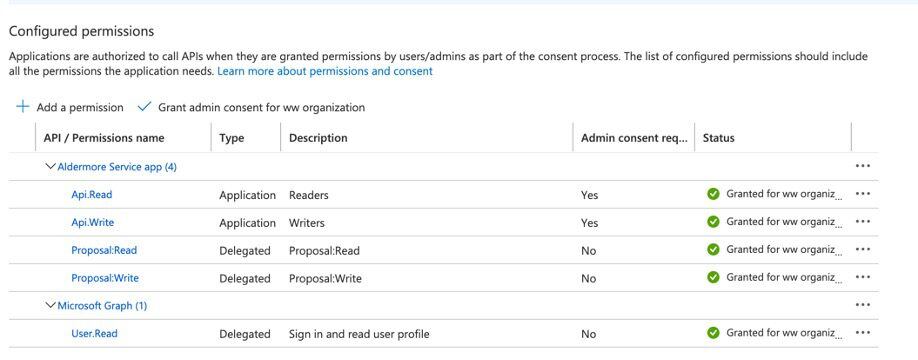
API Manager
From the Anypoint API Manager we make the necessary configurations to integrate with Azure AD:
Anypoint API Manager (API Manager) is a component of Anypoint Platform that enables you to manage, govern, and secure APIs. It leverages the runtime capabilities of API Gateway and Anypoint Service Mesh, both of which enforce policies, collect, and track analytics data, manage proxies, provide encryption and authentication, and manage applications.
- We need to have documentation explaining the API Methods and scopes
- For the example below, we have created the methods assigned to specific scopes of a resource. We can add more resources if we want.
- /GET – GET is used to request data from specified resource.
- /POST- POST is used to send data to a server to create/update a resource.
- /PUT- PUT is used to send data to a server to create/update a resource.
- For Broker Portal, we get success response for GET, PUT and POST method.
- For Lease Soft, we get success response for GET method.

Applying security measures
Policies enable you to enforce regulations to help manage security, control traffic, and improve adaptability of your APIs. In this example, we have used the below policies.
- Client ID Enforcement Policy
The Client ID Enforcement policy restricts access to a protected resource by allowing requests only from registered client applications. The policy ensures that the client credentials sent on each request have been approved to consume the API.
When a client application is registered in Anypoint Platform, a pair of credentials consisting of a client ID and client secret is generated. When the client application requests access to an API, a contract is created between the application and that API.
An API that is protected with a Client ID Enforcement policy is accessible only to applications that have an approved contract. Example of Client id enforcement of my POC.

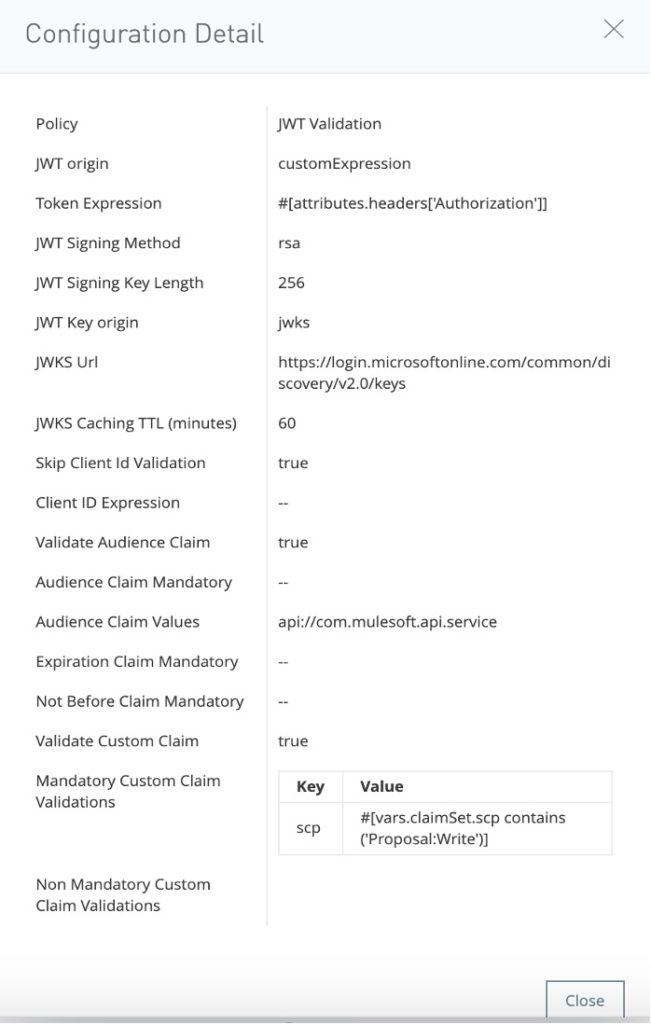
- JWT Validation Policy
JSON Web Token (JWT) is a URL-secure method of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is used as the payload of a JSON Web Signature (JWS), or as a JSON web encryption (JWE) structure in plain text. This enables the claims to be digitally signed and integrity protected with a message authentication code (MAC). Because the token is signed, you can trust the information and its source.
The JWT Validation policy validates the signature of the token and asserts the values of the claims of all incoming requests by using a JWT with JWS format. The policy does not validate JWT that uses JWE.
Broker portal configuration example:
End- to-End Flow between Azure AD and Mule API
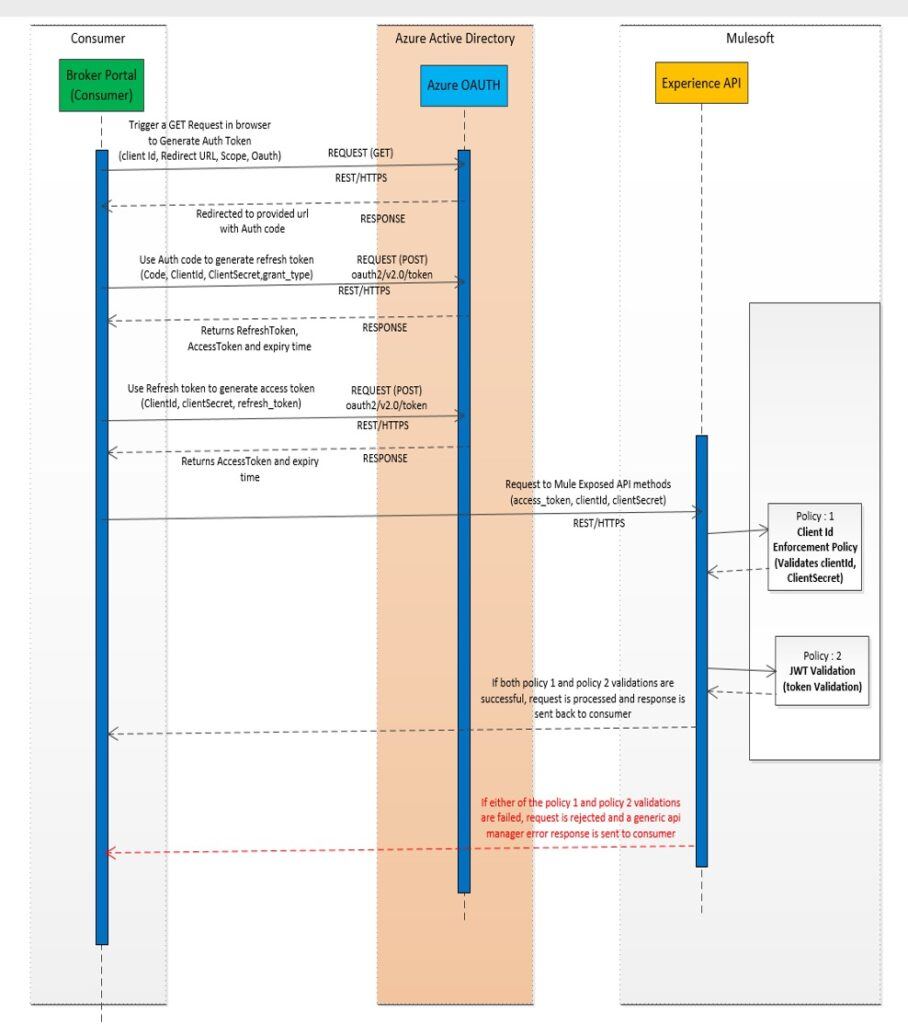
The end-to-end flow includes Token Generation and Token validation:
Token Generation
Generate Auth Token: Client calls /authorises the end point to generate the authorisation code.
Generate access Token: Client calls Azure OAuth token endpoint with Authorisation code grant type, requesting access token and refresh token for the Service API.
Generate Refresh Token: Client calls Azure OAuth token endpoint with Refresh token grant type, returns Access token, which is also a JWT token, with an RSA signature. The JWT Token contains an Audience Claim with the Service API ID.
- Generate Auth Token
The following is the URL, to get the Auth code for Broker Portal.
This token is taken from the endpoints in Azure Portal.
GET request for Authorization code (sample url):
https://login.microsoftonline.com/ --tenant id--/oauth2/v2.0/authorize
- Generate Refresh Token
The following is the URL, to get the Refresh token for Broker Portal.
This token is taken from the endpoints in Azure Portal.
POST request for Refresh token (sample url)
https://login.microsoftonline.com/ --tenant id--/oauth2/v2.0/token
- Generate Access Token:
The following is the URL, to get the Access token for Broker Portal.
This token is taken from the endpoints in Azure Portal.
POST request has been sent here.
https://login.microsoftonline.com/--tenant id--/oauth2/v2.0/token
Token Validation
As Dynamic Client Registration is not supported by Azure, the standard OAuth cannot be implemented. Taking advantage of the Client ID Enforcement and JWT Validation, a Client Application can authorise and authenticate following the OAuth 2.0 protocol anyway, based on these steps:
- Client provides the API access client credentials OAuth/JWT Token to the Mule API.
- JWT Validation Policy configured on API Manager decrypts the JWT Token with Azure public key and validates the Audience Claim and Roles and Scopes.
If you would like to find out more about how to implement OAuth integration with Azure AD using Anypoint Platform, we can help. Give us a call or email us at Salesforce@coforge.com.
Other useful links:
Related reads.


About Coforge.
We are a global digital services and solutions provider, who leverage emerging technologies and deep domain expertise to deliver real-world business impact for our clients. A focus on very select industries, a detailed understanding of the underlying processes of those industries, and partnerships with leading platforms provide us with a distinct perspective. We lead with our product engineering approach and leverage Cloud, Data, Integration, and Automation technologies to transform client businesses into intelligent, high-growth enterprises. Our proprietary platforms power critical business processes across our core verticals. We are located in 23 countries with 30 delivery centers across nine countries.



